Website security is of paramount importance in today’s digital landscape. One of the key tools in this realm is SSL, a technology that encrypts data between users and websites. While SSL provides a crucial layer of protection, it’s not a complete solution. This blog explores the ins and outs of SSL, its limitations, and how Web Application Firewalls (WAFs) step in to enhance website security. We’ll delve into the technicalities, security concerns, and the collaborative approach that keeps websites safe from a multitude of threats.
Understanding SSL
An SSL certificate is a digital document that serves as a crucial component of the Secure Sockets Layer (SSL) protocol. It contains specific information about a website and its owner, including the website’s domain name, its owner’s details, and the digital signature of the Certificate Authority (CA). This digital signature is used to verify the authenticity of the certificate.
Role of SSL Certificates:
SSL certificates play a pivotal role in enhancing the security of websites by enabling encrypted communication between users’ browsers and the website’s server. The primary objectives of SSL certificates are:
- Authentication: SSL certificates serve as a digital credential that verifies the legitimacy of a website’s identity. This is achieved through the inclusion of the website’s domain name and its owner’s information within the certificate. When a user accesses a website, their browser checks the SSL certificate to confirm that the website is genuine and not an imposter attempting to steal sensitive information.
- Data Encryption: One of the fundamental purposes of SSL certificates is to encrypt data during transmission. When information is sent from a user’s browser to the server or vice versa, the SSL certificate ensures that the data is transformed into an unreadable format using complex encryption algorithms. This encrypted data is then transmitted securely over the internet. Even if intercepted by malicious parties, the encrypted data remains indecipherable without the proper decryption key.
- Data Integrity: SSL certificates also ensure the integrity of the data being transmitted. By employing cryptographic hashing techniques, SSL certificates create a unique “fingerprint” of the data before transmission. Upon receipt, the recipient can verify whether the data has been tampered with during transit. If any alterations are detected, the connection is terminated, preventing users from interacting with compromised data.
- Trustworthiness: Websites that use SSL certificates provide users with a sense of security and trust. Modern web browsers display visual cues, such as a padlock icon or “https://” in the address bar, to indicate that the website is secured with SSL. This visual feedback reassures users that their interactions with the website are protected and private.
- Compliance: Many industries and regulations require websites to implement SSL certificates, especially when handling sensitive user data like credit card information or personal details. By adhering to these standards, websites can demonstrate compliance and maintain their reputation.
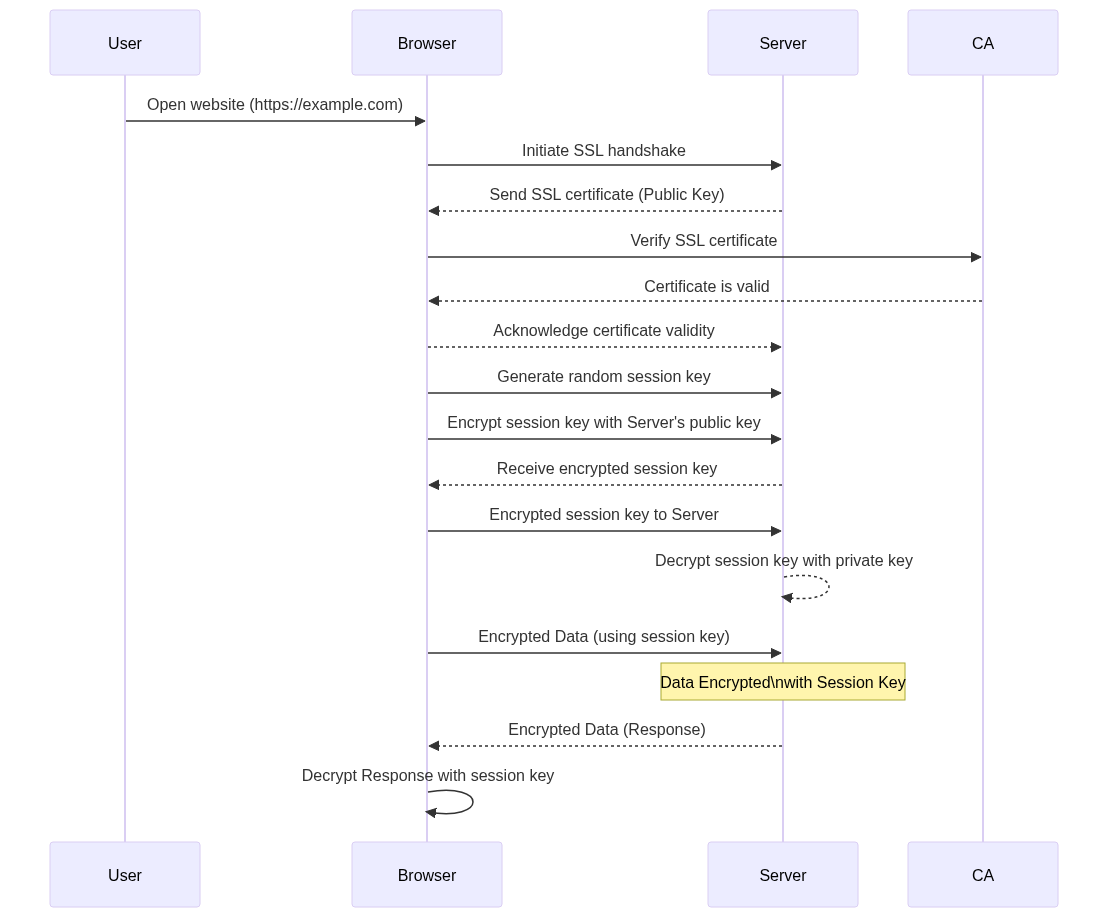
The SSL Handshake Process:
The SSL handshake process is a critical sequence of steps that occurs when a user’s browser initiates a connection with a website secured with SSL. This process establishes the foundation for secure communication by ensuring encryption, authentication, and the exchange of cryptographic keys. Let’s delve into the intricacies of each step:
- Client Hello:
- The process begins when a user enters a website’s URL with “https://” (indicating a secure connection) in their browser’s address bar.
- The browser sends a “Client Hello” message to the website’s server.
- This message contains information about the browser’s supported encryption algorithms and preferences.
- Server Hello:
- Upon receiving the “Client Hello,” the server responds with a “Server Hello” message.
- In the “Server Hello” message, the server selects the strongest encryption algorithm and security settings that both the server and browser can support.
- This negotiation ensures that the highest level of security is established for the connection.
- Key Exchange:
- The server sends its public key to the browser. The public key is a component of the SSL certificate associated with the server.
- The browser generates a random session key, which is a symmetric encryption key unique to the current session. This session key will be used for encrypting and decrypting data during the session.
- The browser encrypts the session key with the server’s public key and sends the encrypted session key back to the server.
- Encryption and Data Exchange:
- With the session key established, both the browser and the server can now encrypt and decrypt data using this shared key.
- The browser generates a symmetric encryption key for the session, which is much faster than asymmetric encryption and is suitable for encrypting large amounts of data.
- The browser and server can now communicate securely by encrypting the data using the session key.
- Authentication:
- SSL certificates contain the website’s public key and digital signature from a trusted Certificate Authority (CA).
- The server’s SSL certificate is sent to the browser during the handshake.
- The browser verifies the certificate’s validity by checking its digital signature against a list of trusted CAs stored in the browser.
- If the certificate is valid and issued by a trusted CA, it confirms the authenticity of the server and ensures that the user is connecting to the intended website.
The SSL handshake process ensures that the connection between the user’s browser and the website’s server is secure, encrypted, and authenticated. By exchanging cryptographic keys, negotiating encryption algorithms, and verifying the server’s identity, the SSL handshake lays the groundwork for a protected and private data exchange. This foundational process sets the stage for secure interactions between users and websites, safeguarding sensitive information from potential threats.
Securing Data in Transit:
Ensuring the security of data during its journey between a user’s browser and a website’s server is a fundamental goal of SSL. The process of securing data in transit involves encryption and mechanisms to prevent eavesdropping and data tampering. Let’s explore each aspect in detail:
- Data Encryption:
- SSL employs powerful encryption algorithms to transform data into an unreadable format before transmission.
- Encryption utilizes complex mathematical operations that convert plaintext data (normal text) into ciphertext (encrypted text) using an encryption key.
- The session key, generated and exchanged during the SSL handshake, is used as the encryption key.
- This encrypted data is transmitted over the internet, and only parties with the corresponding decryption key (session key) can decipher the data.
- Preventing Eavesdropping:
- Eavesdropping, or interception of data by unauthorized entities, is a significant threat when data is transmitted over the internet.
- SSL encryption ensures that even if intercepted by attackers, the intercepted data remains indecipherable without the session key.
- Attackers attempting to eavesdrop on the communication would encounter encrypted data, making it virtually impossible to gain any meaningful insights from the intercepted information.
- Data Tampering Prevention:
- SSL also addresses the risk of data tampering, where attackers alter the data during transmission to modify its content.
- Cryptographic hashing functions are employed to create unique “fingerprints” (hashes) of the data before it’s transmitted.
- The recipient can compute the hash of the received data and compare it with the original hash. Any discrepancy indicates data tampering.
- If tampering is detected, the connection is terminated to prevent users from interacting with compromised data.
- Data Integrity Checks:
- SSL includes mechanisms to verify the integrity of transmitted data.
- The encrypted data, along with a Message Authentication Code (MAC), is transmitted.
- The MAC is a checksum generated using the session key and the encrypted data. It ensures that the data hasn’t been altered during transmission.
- User Privacy and Trust:
- Securing data in transit enhances user privacy by preventing unauthorized parties from intercepting and accessing sensitive information, such as login credentials and personal details.
- As browsers display visual cues (like a padlock icon) to indicate a secure connection, users are more likely to trust websites that use SSL to protect their data.
By encrypting data during transmission and employing mechanisms to prevent eavesdropping and data tampering, SSL ensures the confidentiality, integrity, and authenticity of information exchanged between users and websites. This level of security instills confidence in users and enables them to interact with websites while maintaining the privacy of their sensitive information.
Limitations of SSL
While SSL plays a crucial role in establishing secure connections and encrypting data, it’s important to acknowledge its limitations. Let’s explore these limitations across different parameters:
| Parameter | SSL Limitations |
|---|---|
| Encryption | SSL focuses on encrypting data in transit, but the data might still be exposed at the endpoints. |
| Man-in-the-Middle Attacks | Attackers can intercept communication between the user and server, despite SSL. |
| Certificate Vulnerabilities | SSL certificates can be misconfigured or compromised, leading to security risks. |
| SSL Stripping | Attackers can force users onto unencrypted connections, bypassing SSL. |
| Limited Protection against Application Layer Attacks | SSL doesn’t offer comprehensive protection against application-layer attacks like SQL injection and Cross-Site Scripting (XSS). |
Enabling SSL encryption can impact website performance due to computational overhead.
Let’s see these limitations one by one.
- Encryption:
While SSL effectively encrypts data during transmission, it’s important to note that data might still be exposed at the endpoints—where it’s decrypted before use. Once data reaches its destination, it’s decrypted for processing, leaving it vulnerable to attacks targeting the server or the user’s device. - Man-in-the-Middle Attacks:
Despite SSL’s encryption, attackers can execute man-in-the-middle attacks by intercepting and relaying communication between the user and the server. These attacks can occur when attackers position themselves between the two endpoints, intercepting data before it’s encrypted or after it’s decrypted. This underscores the need for robust authentication and certificate validation processes. - Certificate Vulnerabilities:
SSL certificates can become points of vulnerability if not managed properly. Misconfigured or compromised certificates can undermine the trustworthiness of the SSL connection. For instance, expired or incorrectly configured certificates can lead to browser warnings or allow attackers to impersonate a legitimate website. - SSL Stripping:
Attackers can employ a technique known as SSL stripping to force users onto unencrypted connections, bypassing SSL. This involves intercepting the initial HTTPS request from the user and downgrading it to an HTTP connection, allowing attackers to eavesdrop on the data exchange between the user and the server. - Limited Protection against Application Layer Attacks:
SSL is primarily designed to encrypt data and secure the communication channel, but it doesn’t provide comprehensive protection against application-layer attacks. Threats like Cross-Site Scripting (XSS) and SQL injection can exploit vulnerabilities in the website’s code, potentially compromising user data despite the presence of SSL. - Performance Impact:
Implementing SSL encryption can introduce a performance overhead. The process of encrypting and decrypting data requires additional computational resources, potentially slowing down website load times. Balancing the benefits of security with performance considerations is crucial.
Understanding these limitations of SSL is essential for website administrators and developers. By recognizing these constraints, they can implement additional security measures to mitigate risks and create a more robust defense against various threats.
HTTP Security Headers:
In web security, where protecting against a diverse range of cyber threats is paramount, HTTP security headers emerge as a crucial defense mechanism. These headers are an essential component of the Hypertext Transfer Protocol (HTTP) that web browsers and servers use to communicate. They provide a means to enhance the security posture of websites by adding an extra layer of protection against various types of attacks. Let’s delve into the significance of HTTP security headers and explore some of the prominent headers used to fortify website security.
HTTP security headers are small pieces of information added to the HTTP response sent by a web server to a browser. These headers convey instructions to the browser on how to interact with the website and its content. Their primary objective is to bolster security by mitigating specific risks associated with web applications. By instructing browsers to behave in specific ways, these headers offer valuable safeguards against potential vulnerabilities and attacks.
Key Roles of HTTP Security Headers:
- Content Security Policy (CSP):
Content Security Policy (CSP) is a vital HTTP security header that helps prevent Cross-Site Scripting (XSS) attacks. XSS attacks occur when malicious scripts are injected into web pages, potentially compromising user data or spreading malware. CSP enables website owners to define the sources from which scripts and resources can be loaded, reducing the risk of unauthorized script execution. - Strict Transport Security (HSTS):
Strict Transport Security (HSTS) is designed to address the threat of protocol downgrade attacks and session hijacking. When a website implements HSTS, it instructs browsers to always use secure connections (HTTPS) to communicate with the site, even if the user tries to access the site via an insecure HTTP link. This prevents attackers from intercepting or manipulating the communication between the user and the server. - X-Frame-Options:
X-Frame-Options mitigate clickjacking attacks by controlling how a website can be embedded within an iframe. Clickjacking involves tricking users into clicking on an element in a different context than they expected. With X-Frame-Options, website owners can prevent their pages from being loaded within iframes on other websites, reducing the risk of clickjacking exploits.
Implementation and Configuration:
Implementing and configuring HTTP security headers involves adding them to the server’s HTTP response. The headers can be set using directives that specify the desired behavior. This process can be accomplished via web server configuration or application-level code, depending on the web framework being used.
Benefits and Challenges:
HTTP security headers provide several advantages, including enhanced protection against specific attack vectors and improved compliance with security best practices. However, their implementation can be complex and require careful testing to ensure they don’t inadvertently disrupt the website’s functionality.
Here are the benefits and challenges of using security headers:
| Benefits | Challenges |
|---|---|
| 1. Enhanced Security: Security headers provide an additional layer of protection against specific types of attacks, such as XSS and clickjacking. | 1. Configuration Complexity: Implementing security headers requires a solid understanding of the headers’ functionalities and how they interact with web applications. |
| 2. Attack Mitigation: Security headers help prevent or reduce the impact of common web vulnerabilities, contributing to a more secure online environment. | 2. Compatibility Concerns: Some security headers might not be supported by older browsers, potentially causing compatibility issues for users on outdated systems. |
| 3. Compliance: Incorporating security headers aligns with industry standards and best practices for web security, demonstrating a commitment to safeguarding user data. | 3. Overblocking Risk: Incorrectly configured security headers can unintentionally block legitimate website functionality, leading to user frustration. |
| 4. User Trust: Implementing security headers enhances user trust by demonstrating a proactive approach to website security, encouraging users to interact with the site confidently. | 4. Testing and Debugging: Properly configuring security headers requires thorough testing to ensure they don’t disrupt the user experience or create unexpected issues. |
| 5. Reduced Attack Surface: Security headers narrow the attack surface by implementing security measures that minimize the potential points of vulnerability. | 5. Updates and Maintenance: As web application technologies evolve, security headers might need adjustments to remain effective, requiring ongoing maintenance and updates. |
Incorporating HTTP security headers is a proactive approach to bolstering website security. These headers contribute significantly to preventing and mitigating various attack vectors, such as XSS, clickjacking, and session hijacking. By employing the right combination of security headers and configuring them effectively, website owners can establish a robust defense against common web application vulnerabilities. As we move forward, it’s essential for developers and website administrators to prioritize the integration of HTTP security headers as part of their comprehensive security strategy.
Addressing Security Issues
In the dynamic landscape of web security, websites often face an array of potential vulnerabilities and threats that can compromise the integrity, confidentiality, and availability of data. Addressing these security issues is of paramount importance to ensure a robust defense against cyberattacks. Here, we’ll delve into major security issues commonly encountered in websites and explore effective mitigation strategies.
| Security Issue | Mitigation Strategy |
|---|---|
| 1. Cross-Site Scripting (XSS) | Implementation of Content Security Policy (CSP): CSP helps prevent XSS attacks by defining trusted sources from which scripts can be executed. It restricts the ability of attackers to inject and execute malicious scripts. |
| Input Validation and Sanitization: Ensure that user input is properly validated and sanitized to prevent malicious code from being executed. | |
| 2. SQL Injection | Use Prepared Statements and Parameterized Queries: These techniques prevent SQL injection by separating user input from SQL queries. |
| Escaping User Input: Special characters within user input should be properly escaped before being used in SQL queries to prevent unauthorized database access. | |
| 3. Cross-Site Request Forgery (CSRF) | Implementing Anti-CSRF Tokens: Generate and validate unique tokens for each user session to verify the legitimacy of requests. |
| Same-Site Cookies: Set cookies with the “SameSite” attribute to ensure that cookies are only sent in same-site requests, reducing the risk of CSRF attacks. | |
| 4. Security Misconfigurations | Regular Security Audits: Conduct periodic security audits to identify and rectify misconfigurations in server settings, databases, and applications. |
| Least Privilege Principle: Restrict access rights and permissions to only what is necessary for each user and component. | |
| 5. Insecure Authentication and Session Management | Use Strong Authentication Mechanisms: Implement multi-factor authentication (MFA) and strong password policies to enhance user authentication. |
| Secure Session Management: Generate unique session IDs, use secure cookies, and set session expiration times to mitigate session hijacking. | |
| 6. Inadequate Data Validation | Validation and Sanitization: Validate and sanitize all user input and data, both on the client and server sides. |
| Input Length Limitation: Implement limits on input lengths to prevent buffer overflows and data manipulation attacks. | |
| 7. Insecure Deserialization | Implement Input Validation: Validate serialized data before deserializing it to prevent malicious payloads. |
| Use Trusted Serialization Libraries: Utilize well-known and trusted serialization libraries that implement security measures against deserialization attacks. | |
| 8. Insufficient HTTPS Usage | Enable HTTPS Everywhere: Use HTTPS for all communications, ensuring end-to-end encryption and preventing data interception. |
| Implement HTTP Security Headers: Use security headers like HSTS and CSP to fortify HTTPS usage and protect against various attacks. | |
| 9. Lack of Input and Output Encoding | Implement Proper Encoding: Encode user input before displaying it in web pages to prevent XSS attacks. |
| Use Framework Security Features: Utilize built-in security features provided by web frameworks to automatically encode output. | |
| 10. Vulnerable Third-Party Components | Regularly Update Components: Keep third-party libraries and components up to date to patch known vulnerabilities. |
| Monitor Security Advisories: Subscribe to security advisories for third-party components and promptly apply recommended updates. |
By systematically addressing these major security issues and implementing the corresponding mitigation strategies, website owners, developers, and administrators can significantly enhance the security posture of their web applications. Regular security assessments, proactive measures, and a commitment to staying informed about emerging threats are essential components of a comprehensive security approach.
Web Application Firewall (WAF)
Web Application Firewall (WAF) emerges as a critical component in modern cybersecurity strategies, providing an additional layer of defense against a wide range of web-based attacks. WAFs act as a shield for web applications, helping to mitigate threats and vulnerabilities that traditional security measures might not fully address. Let’s delve into the realm of WAFs, exploring what they are, how they work, and their role in bolstering website security over SSL.
A Web Application Firewall (WAF) is a specialized security solution designed to protect web applications from various types of cyber threats, such as SQL injection, Cross-Site Scripting (XSS), and Distributed Denial of Service (DDoS) attacks. Unlike traditional firewalls that focus on network traffic, WAFs operate at the application layer, scrutinizing the content and behavior of incoming and outgoing traffic. WAFs can be hardware-based appliances, software applications, or cloud-based services.
How does Web Application Firewall work?
Web Application Firewalls (WAFs) serve as intelligent gatekeepers that protect web applications from a myriad of cyber threats. Their effectiveness lies in their ability to operate at the application layer, where they can scrutinize and filter incoming and outgoing traffic. Let’s look into how WAFs work to safeguard web applications:
- Traffic Analysis:
WAFs start by analyzing the traffic that enters or exits the web application. This includes examining the HTTP requests and responses, including headers, content, and other attributes. This in-depth analysis allows the WAF to understand the nature of the communication and identify potential security risks. - Rule Enforcement:
WAFs implement a set of predefined security rules and policies that determine whether incoming or outgoing traffic exhibits signs of malicious intent or vulnerabilities. These rules cover a wide range of attack vectors, such as SQL injection, Cross-Site Scripting (XSS), and more. The rules are tailored to detect specific patterns, behaviors, and anomalies that are indicative of an attack. - Signature-Based Detection:
A common method used by WAFs is signature-based detection. This involves comparing the attributes of incoming traffic against a database of known attack signatures. If a match is found, the WAF takes action to block or mitigate the threat. This approach is effective for detecting well-known attacks with identifiable patterns. - Behavioral Analysis:
Advanced WAFs employ behavioral analysis to identify anomalies in traffic patterns. Instead of relying solely on predefined signatures, these WAFs analyze the typical behavior of the web application and its users. If traffic deviates from the established baseline, the WAF may consider it suspicious and take appropriate measures. - Positive and Negative Security Models:
WAFs use two primary security models: positive security and negative security. In the positive security model, only known valid patterns and behaviors are allowed, effectively blocking any traffic that doesn’t adhere to these patterns. In the negative security model, the WAF blocks traffic that matches known attack patterns. The combination of both models provides a comprehensive approach to protection. - Learning and Adaptation:
Some modern WAFs incorporate machine learning and AI algorithms to continuously learn from traffic patterns and behaviors. Over time, these WAFs adapt to new and emerging threats that may not have established signatures. This proactive approach enables them to detect zero-day vulnerabilities and threats that are not yet widely recognized. - Action:
When the WAF detects traffic that violates security rules, it takes appropriate action based on the configured policies. This could involve blocking malicious traffic, filtering out harmful content, or alerting administrators about potential threats. - Continuous Monitoring:
WAFs continuously monitor the web application’s traffic to detect evolving threats. They provide real-time insights into the security posture of the application and enable administrators to respond swiftly to any potential breaches.
How WAF protects our website over SSL?
When it comes to SSL-protected websites, WAFs play a crucial role in enhancing security:
- SSL Termination: WAFs can terminate SSL connections on behalf of the web server. This enables them to inspect and analyze encrypted traffic for malicious content, even if the original communication was encrypted with SSL.
- Threat Detection: WAFs can identify patterns and behaviors associated with known attack vectors, even when encrypted through SSL. This includes detecting malicious code or payloads hidden within encrypted traffic.
- Prevention of Exploits: If the WAF detects an attack or malicious intent within encrypted traffic, it can take immediate action to prevent the exploit from reaching the web application, safeguarding sensitive data.
- Behavioral Analysis: Some WAFs use behavioral analysis to detect anomalies in encrypted traffic, even if the exact attack is unknown. This proactive approach helps identify zero-day vulnerabilities and emerging threats.
In summary, WAFs provide a comprehensive security layer for web applications, complementing the protection offered by SSL. By inspecting and analyzing traffic, enforcing security rules, and adapting to evolving threats, WAFs contribute to a fortified defense against a multitude of cyber threats, ensuring the confidentiality, integrity, and availability of websites.
Synergy of Security Layers
In the complex landscape of cybersecurity, the concept of a layered defense strategy has gained prominence. This approach involves combining multiple security layers, each addressing specific aspects of protection, to create a comprehensive and robust shield against a wide range of threats. The synergy between Web Application Firewalls (WAFs), SSL encryption, and other security measures exemplifies the effectiveness of this layered approach. Let’s explore how these security layers collaborate to enhance the overall security posture of web applications:
- SSL Encryption as the Foundation:
SSL encryption forms the foundational layer of security. It establishes a secure communication channel between users and websites, encrypting data during transmission to prevent eavesdropping and data tampering. SSL’s encryption ensures that sensitive information, such as login credentials and financial data, remains confidential even when traversing potentially insecure networks. - Web Application Firewall (WAF) as the Sentry:
Building upon SSL encryption, the Web Application Firewall (WAF) serves as a sentinel guarding the application layer. By actively inspecting traffic, the WAF detects and mitigates a wide range of threats, including SQL injection, XSS attacks, and more. The WAF’s ability to analyze decrypted traffic enables it to identify and thwart malicious activities that might bypass SSL encryption. - Comprehensive Threat Detection and Prevention:
The synergy between SSL and WAF ensures a comprehensive approach to threat detection and prevention. SSL encryption protects data in transit, while the WAF scans for malicious intent within the encrypted traffic. This combination effectively shields against both external attacks and potential insider threats, enhancing the overall security posture. - Adaptive Defense:
WAFs that employ machine learning and behavioral analysis enhance the adaptive nature of the security layers. While SSL and traditional security measures address known threats, the WAF’s ability to learn from traffic patterns enables it to identify zero-day vulnerabilities and emerging threats. This adaptive defense mechanism fortifies the resilience against evolving attack vectors. - Mitigation of Emerging Threats:
The WAF’s real-time protection capabilities come into play when new vulnerabilities are identified. As attackers develop innovative methods to exploit web applications, the WAF’s continuous monitoring and immediate action can thwart attacks even before they gain traction. This proactive approach helps in minimizing the potential impact of security breaches. - Reduced Attack Surface:
The collaboration between SSL and WAF results in a reduced attack surface. SSL encryption prevents the interception of sensitive data, while the WAF intercepts and neutralizes malicious traffic before it reaches the application. This minimizes the opportunities for attackers to exploit vulnerabilities, making it significantly harder for them to breach the defenses. - Multi-Layered Resilience:
The synergy of security layers exemplifies the principle of defense in depth. By combining the protective capabilities of SSL, WAFs, and other security measures, web applications gain multi-layered resilience. Even if one layer is compromised, the others continue to provide a barrier against threats, significantly enhancing the overall security posture.
In summary, the synergy between SSL encryption and Web Application Firewalls represents a formidable defense strategy against a wide array of cyber threats. This layered approach leverages the strengths of each security layer to create a comprehensive shield that addresses different attack vectors and vulnerabilities.
Conclusion
In website security, the protection of sensitive data and the prevention of cyber threats are paramount. While SSL encryption forms the foundation by securing data in transit, the integration of Web Application Firewalls (WAFs) takes security to a higher level. WAFs actively inspect traffic, detect vulnerabilities, and shield against a wide array of attacks, ensuring the integrity, confidentiality, and availability of web applications.
By working in synergy, SSL and WAFs create a multi-layered defense strategy that leaves no room for complacency. SSL encryption guards against data interception during transmission, while WAFs act as vigilant sentinels, monitoring for malicious activity within encrypted traffic. This combined approach provides comprehensive protection against known and emerging threats, enhancing the overall security posture.
In the digital landscape where cyber threats continue to evolve, the collaboration between SSL and WAFs remains an essential component of website security. This partnership empowers developers, administrators, and businesses to establish a resilient defense against the ever-present risk of cyberattacks. By implementing SSL encryption and integrating Web Application Firewalls, websites can inspire confidence among users and ensure a safer online experience for all.