Follow Us:
Advanced Firebase Security Rules for Realtime Database

Firebase Realtime Database offers a flexible, NoSQL cloud database to store and sync data between users in real time. To safeguard this data, Firebase provides a set of Security Rules that govern how data is accessed and manipulated. These rules are crucial for ensuring that only authenticated and authorized users can read or write to certain parts of the database, thus maintaining data integrity and privacy.
This blog delves into the advanced aspects of Firebase Security Rules, guiding developers through crafting sophisticated rulesets that align with complex application requirements. We will explore the nuances of rule configuration, from user authentication integration to performance optimization for large-scale applications. Whether you are a seasoned developer or a computer science student, the insights shared here will enhance your ability to secure Firebase databases effectively.
Our focus will be on utilizing Firebase Security Rules to their fullest potential, ensuring that our database interactions are secure, efficient, and maintainable. Let’s dive into the advanced configurations that can help protect your Firebase Realtime Database.
Understanding Firebase Security Rules:
Firebase Security Rules are sets of server-side scripts that define how your data should be structured and when your data can be read from or written to. These rules are used to validate incoming data against certain conditions before it’s allowed to be stored in your Firebase Realtime Database or Cloud Firestore. They provide a flexible and expressive syntax that allows for complex rule definitions, ensuring that your app’s data remains secure by controlling access based on authentication status, data validation, and query optimization. Firebase Security Rules enable developers to enforce user permissions and data integrity without the need for an additional server-side validation layer.
Why Firebase Security Rules are Needed?
Security rules are needed to:
- Enforce Data Privacy: Restrict data access to authorized users, ensuring that sensitive information remains confidential.
- Validate Data: Check the data being added or updated against predefined criteria to maintain data integrity and prevent corruption.
- Regulate Data Access: Define which parts of the database can be read or written to by which users, under what conditions.
- Minimize Data Breaches: Act as the first line of defense against unauthorized access and potential database exploits.
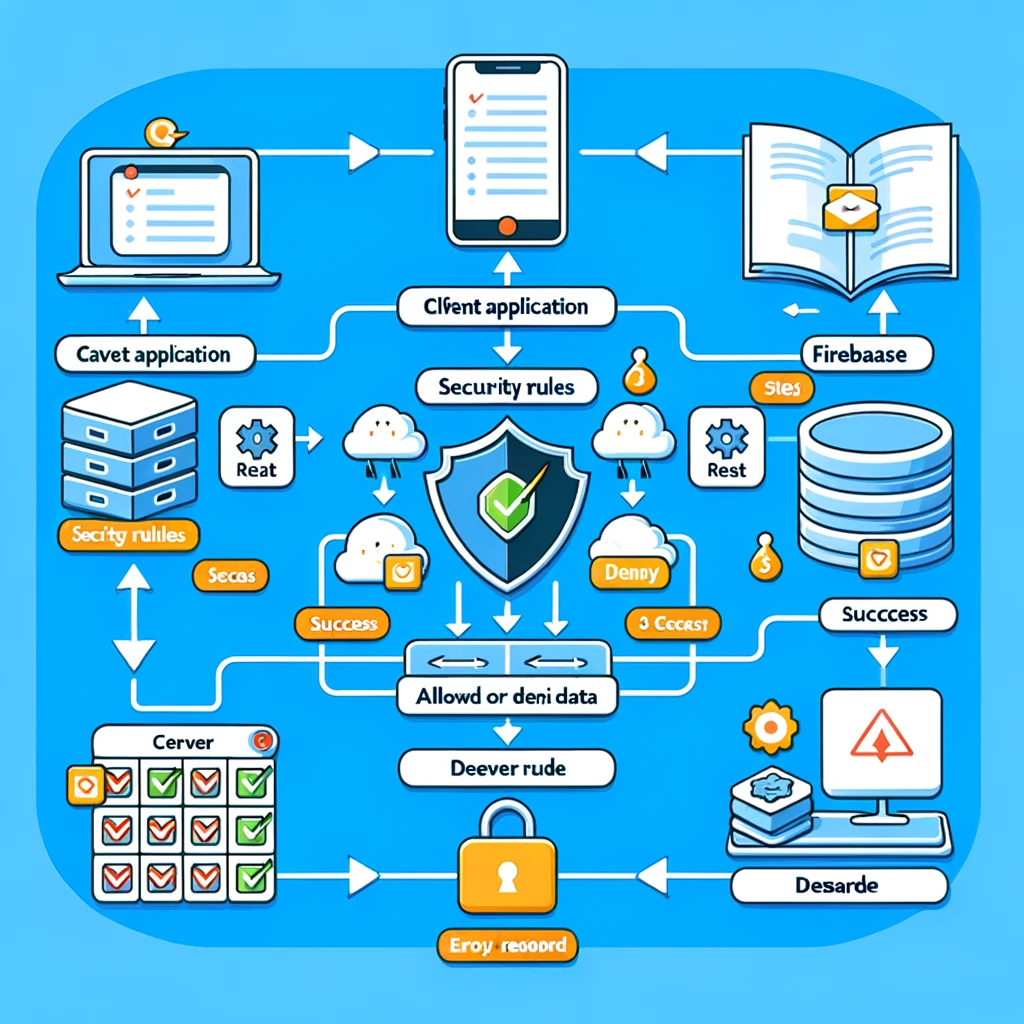
How Security Rules Work?
The diagram above visually depicts the sequence of events that occur when Firebase Security Rules are evaluated in response to a client’s request. Here’s how the workflow operates according to the diagram:
- Client Request: It all begins with the client application, which attempts to perform a read or write operation on the Firebase Realtime Database.
- Firebase Evaluation: This request is sent to Firebase, where it encounters the Security Rules. Before any data is read from or written to the database, Firebase evaluates these rules on the server side to determine if the request is allowed.
- Rules Decision: Firebase Security Rules act as gatekeepers. They contain conditions that must be met for the request to proceed. If the request satisfies the rules, Firebase allows the operation; if not, the request is denied.
- Client Response: After the decision has been made, Firebase sends a response back to the client application. If the rules allowed the operation, the client would receive a successful response, indicating that the read or write has been completed as requested. If the rules denied the operation, the client would receive an error response, indicating that the operation could not be performed.
Throughout this process, the Security Rules ensure that only authorized and authenticated actions are taken upon the database, thus upholding the security and integrity of the data within.
Types of Firebase Security Rules:
Firebase Security Rules are primarily divided into three types, each serving a different aspect of database security and data integrity: Read, Write, and Validate. Below are examples of each rule type with code snippets that demonstrate their typical structure and usage.
1. Read Rules:
These rules determine who can read data from your database. A read rule can be applied globally or to specific nodes within the database.
Example:
{
"rules": {
"users": {
"$uid": {
".read": "$uid === auth.uid"
}
}
}
}In this example, the read rule ensures that a user can only read data from their user node, identified by their unique user ID ($uid), which must match their authenticated UID (auth.uid).
2. Write Rules:
Write rules control who is allowed to write data, including adding, editing, or deleting data in your database.
Example:
{
"rules": {
"users": {
"$uid": {
// Users can write to their own data node
".write": "$uid === auth.uid"
}
}
}
}Here, the write rule specifies that users can only perform write operations on their own data node, similar to the read rule above.
3. Validate Rules:
Validate rules are used to ensure that the data written to the database is in the correct format or meets certain criteria. This can include data type validation, checking the structure of the data, or even ensuring that data values fall within a specific range.
Example:
{
"rules": {
"users": {
"$uid": {
"age": {
// Validates that age is a number between 0 and 150
".validate": "newData.isNumber() && newData.val() >= 0 && newData.val() <= 150"
},
"email": {
// Validates that the email is a string and contains an @ symbol
".validate": "newData.isString() && newData.val().matches(/^.+@.+$/)"
}
}
}
}
}In this validation example, we are ensuring that age is a number within a logical range and that email is a string formatted like an email address.
These rules are written in Firebase’s JSON-based rules language and are deployed to your Firebase project where they are enforced by the Firebase Realtime Database service. It’s important to test your rules using the Firebase console, simulator, or the Firebase Emulator Suite to ensure they work as intended before deploying them to production.
Advanced Rule Definitions
In Firebase, advanced rule definitions allow developers to create more sophisticated and granular access controls for their Firebase Realtime Database. This section will delve into the use of variables, data types, functions, and regular expressions in rule definitions, as well as the distinction between server-side and client-side rule enforcement.
- Variables and Data Types in Rules: Firebase Security Rules support variables and data types to make rules dynamic and context-aware. Here’s an example showcasing how to use them:
{
"rules": {
"posts": {
"$postId": {
// Variables: $postId represents the dynamic ID of a post
".write": "auth != null && (!data.exists() || data.child('authorId').val() === auth.uid)",
// Data Types: Using boolean expressions to check if data exists and comparing strings for author ID
".read": "auth != null && data.child('public').val() === true"
}
}
}
}In this code snippet, $postId is a variable representing each post’s unique ID. The write rule uses a boolean expression to ensure that the user is authenticated (auth != null) and either the data does not exist (indicating a new post) or the user is the author of the post. The read rule also checks for authentication and additionally ensures that the post is marked as public.
- Functions and Regular Expressions: Functions like
auth.uid,data.exists(),data.val(), andnewData.val()are used to retrieve data or make decisions based on the current authentication state or database data. Regular expressions can validate the format of the data.
{
"rules": {
"users": {
"$uid": {
"email": {
// Regular Expression: Ensures the email address is properly formatted
".validate": "newData.isString() && newData.val().matches(/^[^@]+@[^@]+.[^@]+$/)"
}
}
}
}
}In this example, newData.isString() checks that the new data is a string, and newData.val().matches() uses a regular expression to validate the format of an email address.
- Server-side vs. Client-side Enforcement: All Firebase Security Rules are enforced on the server side, meaning that they are evaluated at Firebase servers, not on the client device. This server-side enforcement ensures that rules are not bypassed by a client-side environment that has been compromised or is running malicious code.
{
"rules": {
".read": "false", // No client can read data from the database
".write": "false" // No client can write data to the database
}
}In this simplistic example, the rules universally reject all reads and writes on the client side by setting them to false. These rules are enforced server-side, so even if a client application were modified to ignore these rules, the Firebase server would still enforce them and deny access.
Advanced rule definitions provide robust tools for securing your Firebase Realtime Database. It’s critical to thoroughly test these rules in a controlled environment to ensure they operate as intended and provide the necessary level of security for your database.
User Authentication and Rules
Firebase Security Rules can be tightly integrated with Firebase Authentication to create secure, user-specific access controls. By leveraging authentication, rules can be crafted to allow access based on a user’s sign-in state, their unique ID, or even based on more complex criteria such as user roles or groups. This section will cover how to create rules that are contingent on user authentication status.
Integrating Firebase Authentication:
Authentication in Firebase is managed by a token that identifies the user. This token is automatically included in every request and can be used in security rules to make access decisions.
{
"rules": {
"user_data": {
"$userId": {
// Only authenticated users can access their data
".read": "$userId === auth.uid",
".write": "$userId === auth.uid"
}
}
}
}In this code snippet, the rules use the auth variable, which contains the authentication token provided by Firebase Authentication. The auth.uid property is the user’s unique identifier, and it’s used here to grant a user read and write access only to their own data.
Rules Based on User ID:
The auth.uid property is key in creating user-specific rules. Here’s how you can restrict access based on the user ID:
{
"rules": {
"user_profiles": {
"$userId": {
// Profile can be read by the user with the matching ID
".read": "$userId === auth.uid",
// Profile can only be created or updated by the matching user ID
".write": "!data.exists() || data.child('userId').val() === auth.uid"
}
}
}
}This example ensures that users can only read their own profile and can create or update their profile only if it doesn’t exist already or if they’re the same user as the one specified in the data.
Role-Based Access Control:
For more advanced scenarios, such as implementing roles, you might store role information within the database or as part of the authentication token. Firebase Security Rules can interpret this information to grant or restrict access.
{
"rules": {
"admin_content": {
// Only users with the admin role can read or write
".read": "auth.token.admin === true",
".write": "auth.token.admin === true"
},
"user_content": {
// Users can read content if their role is at least 'user'
".read": "auth.token.role === 'user' || auth.token.role === 'admin'",
// Users can only add content if they are authenticated
".write": "auth != null && newData.child('createdBy').val() === auth.uid"
}
}
}In the code above, auth.token.admin and auth.token.role are custom claims that you can set in the Firebase Authentication token. These claims are used to determine if the authenticated user has the ‘admin’ role or at least a ‘user’ role.
By integrating Firebase Authentication with Security Rules, you ensure that data access is properly gated behind user identity and roles. These rules form the backbone of a secure, multi-user application where users can safely interact with the database according to the permissions you’ve defined.
Data Validation Rules
Data validation rules are critical in the Firebase Realtime Database to ensure the integrity and format of the data stored. These rules are executed before any data is written to the database, regardless of whether the write operation comes from a direct database set, update, or even as part of a transaction.
Structuring Write Rules for Data Integrity:
Validation rules allow you to enforce the structure and content of the data in your database. They are defined using the .validate key within your rules.
{
"rules": {
"products": {
"$productId": {
// Ensures that each product has a name and a price
".validate": "newData.hasChildren(['name', 'price'])",
"name": {
// Validates that the name is a non-empty string
".validate": "newData.isString() && newData.val().length > 0"
},
"price": {
// Validates that the price is a positive number
".validate": "newData.isNumber() && newData.val() > 0"
}
}
}
}
}In the example above, newData.hasChildren(['name', 'price']) ensures that the required fields ‘name’ and ‘price’ are present in every ‘product’ object. Additional validation rules for ‘name’ and ‘price’ verify the type and constraints of the values.
Conditional Validation Based on Other Data:
You can create conditional validation rules that depend on other data in your database using the data variable, which represents the existing data.
{
"rules": {
"orders": {
"$orderId": {
// Validates that an order's status is 'pending' if it's a new order
"status": {
".validate": "(!data.exists() && newData.val() === 'pending') || (data.exists() && data.val() !== 'pending')"
}
}
}
}
}This snippet demonstrates a rule for an ‘orders’ node where a new order must have a ‘status’ of ‘pending’. If the order already exists, the status can be different.
Complex Data Structures and Arrays:
Firebase Security Rules also allow you to validate more complex data structures, including arrays, by ensuring that each element in an array or each property in an object meets certain criteria.
{
"rules": {
"users": {
"$userId": {
"tags": {
// Validates that each tag is a string
"$tagId": {
".validate": "newData.isString()"
}
}
}
}
}
}In this final example, the rules validate that each element in the ‘tags’ array is a string.
These are just a few examples of the many ways you can use Firebase Security Rules to validate data. The flexibility of these rules allows developers to enforce a wide range of constraints, ensuring that only valid, well-formed data is stored in the database. It’s important to carefully design and test these validation rules to prevent invalid data from being written to your database.
Rules for Data Indexing and Queries
Optimizing data retrieval in Firebase Realtime Database is essential for performance and cost efficiency. Indexing rules help speed up queries on large datasets and ensure that only relevant data is transferred over the network. These rules are defined using the .indexOn key in your Firebase Security Rules.
- IndexOn Rules for Optimizing Queries: The
.indexOnkey is used within your rules to specify which child keys should be indexed by Firebase. This helps to optimize the retrieval of data when querying on these keys.
{
"rules": {
"posts": {
".indexOn": ["status", "timestamp"],
"$postid": {
".read": "auth != null",
".write": "auth != null && auth.uid === data.child('authorId').val()"
}
}
}
}In the code snippet above, the .indexOn directive tells Firebase to index the ‘status’ and ‘timestamp’ keys within the ‘posts’ node. This allows for efficient querying of posts based on their status and timestamp.
- Rules for Securing Indexed Data: While
.indexOnimproves performance, it is also important to ensure that indexed data remains secure. Your read and write rules should be designed to protect indexed data just like any other data.
{
"rules": {
"users": {
".indexOn": ["email"],
"$userid": {
".read": "$userid === auth.uid", // User can only read their own data
".write": "$userid === auth.uid", // User can only write their own data
"email": {
".validate": "newData.isString() && newData.val().matches(/^[^@]+@[^@]+.[^@]+$/)"
}
}
}
}
}In this example, users’ email addresses are indexed to facilitate quick look-ups. However, the read and write rules ensure that a user can only access or modify their own email address, thus securing the indexed data.
Remember that adding indexes for data can affect your database’s performance and the cost of operations. Only fields that are frequently queried should be indexed to avoid unnecessary overhead.
By applying .indexOn to the relevant fields and securing access with proper read and write rules, you can ensure that your Firebase Realtime Database queries are both fast and secure. It’s crucial to balance the need for quick data access with the imperative of maintaining stringent security over your database’s data.
Testing and Debugging Rules
Once Firebase Security Rules are written, it is essential to verify that they function as intended. Testing and debugging are critical steps in this process, allowing developers to ensure that their rules enforce the correct permissions without inadvertently exposing data or allowing unauthorized access.
Simulation Tests in Firebase Console:
The Firebase Console provides a Rules Simulator, which allows developers to test and validate their security rules in a controlled environment before deploying them.
{
"rules": {
"messages": {
".read": "auth != null",
".write": "auth != null && newData.child('uid').val() === auth.uid"
}
}
}With the above rules in place, you can simulate read and write operations in the Firebase Console to verify that messages can only be read by authenticated users and written by users whose UID matches the UID in the message data.
Unit Testing with Firebase Emulator Suite:
For a more robust testing strategy, the Firebase Emulator Suite allows local testing of Security Rules. This suite emulates the behavior of Firebase services on your local machine, enabling comprehensive unit testing.
To perform unit tests, you would write tests in your chosen framework (e.g., Mocha, Jest) and execute them against the emulated database to verify the behavior of your rules.
// Pseudocode for a unit test checking write permission
it('should allow users to write their own data', () => {
const db = firebase.initializeTestApp({ uid: "user_id" }).database();
const ref = db.ref('users/user_id');
return ref.set({ /* user data */ }).then(() => {
// Assert that the write was allowed
});
});In this pseudocode example, a unit test is written to ensure that a user can write to their own data node.
Logging and Interpreting Errors:
When testing rules, both in the simulator and using the emulator, it is crucial to understand the errors returned. Firebase provides detailed error messages that can help diagnose issues with your rules. Analyzing these errors can inform you whether access was denied due to authentication issues, data validation failures, or other rule misconfigurations.
Testing and debugging Firebase Security Rules is an ongoing process. As your application evolves and new features are added, your rules will also need to be updated and retested. By utilizing the simulation and unit testing tools provided by Firebase, and by carefully reviewing error messages, you can ensure that your database remains secure and functions as expected. This proactive approach to testing will help prevent security breaches and data integrity issues in your Firebase Realtime Database.
Conclusion
In conclusion, advanced security rules for Firebase Realtime Database are essential for safeguarding your application’s data. This blog has provided a comprehensive guide to understanding and implementing these rules effectively. We have covered the nuances of rule definitions, the integration of user authentication, the intricacies of data validation, the importance of indexing for efficient queries, and the best practices for testing and debugging these rules.
Securing a real-time database requires diligence and an understanding of potential security vulnerabilities. Firebase Security Rules offer a powerful and flexible way to protect your database by controlling how data is accessed and manipulated. It’s imperative that developers invest the time to write, test, and maintain these rules throughout the lifecycle of their applications.
As Firebase continues to evolve, staying updated on the latest features and security best practices will ensure that your database remains robust against threats while providing a seamless experience for your users. Remember, security is not a one-time setup but an ongoing commitment to protecting your users and their data.