Privacy concerns are growing as more of our daily lives move online. Commercial VPNs, while commonly used, often fall short when it comes to complete security and transparency. Issues such as data logging, limited customization, high subscription fees, and reliance on third-party providers can make them less than ideal for those who value full control over their online activity. These concerns drove me to build my own VPN using AWS EC2 and OpenVPN.
A personal VPN goes beyond basic privacy tools by offering full control over its configuration and operation. It encrypts your internet traffic, secures sensitive data on public networks, and ensures your online activity cannot be tracked. Additionally, it provides the flexibility to tailor the VPN to meet specific needs, such as bypassing regional restrictions or securing private servers, all without the drawbacks of commercial providers.
Building your own VPN may sound technical, but with the right guidance, it becomes straightforward and highly rewarding. In this blog, I will share the exact steps I followed to create my personal VPN, starting from the basics of VPN technology to deploying and using the solution. By the end, you’ll have the knowledge and tools to create your own secure, cost-effective VPN tailored to your needs.
Let’s begin by understanding what a VPN is and why it’s a powerful tool for protecting your online presence.
Understanding VPNs
Virtual Private Networks (VPNs) are vital tools for safeguarding online activity in today’s interconnected world. They create secure, encrypted tunnels between your device and the internet, shielding your data from prying eyes. To build and use a personal VPN effectively, it’s essential to understand the underlying technology, its role in enhancing privacy, and why OpenVPN is an excellent choice for this purpose.
Let’s start with the basics: what exactly is a VPN, and how does it work?
What is a VPN?
A VPN, or Virtual Private Network, is a technology that establishes a secure and encrypted connection between your device and a remote server. This connection, often referred to as a “tunnel,” ensures that all data passing through it is encrypted, making it unreadable to anyone who might intercept it. The VPN then forwards your requests to the internet, masking your actual IP address and replacing it with the VPN server’s IP.
In simple terms, a VPN acts like a protective middleman between your device and the internet. Here’s how it works step by step:
- Device Connection: When you connect to a VPN, your device first establishes a secure link with a VPN server.
- Encryption: Data sent from your device is encrypted before leaving it, ensuring it cannot be read by hackers, network administrators, or malicious actors.
- IP Masking: The VPN server assigns your connection a new IP address, hiding your actual location and preventing websites or trackers from identifying you.
- Data Forwarding: Encrypted data is forwarded from the VPN server to its intended destination, such as a website or an online service. Similarly, responses are encrypted and sent back to your device.
This process ensures that anyone monitoring your connection, such as on public Wi-Fi networks or even your internet service provider, cannot view or manipulate your online activity.
How Does a VPN Protect You?
A VPN safeguards your online activity by encrypting your internet traffic and masking your IP address. This dual-layer protection ensures that sensitive data, such as passwords, personal information, or browsing habits, remains inaccessible to hackers, internet service providers (ISPs), or even surveillance agencies.
To understand how a VPN protects you, it’s important to first see how the internet works without one. Let’s break this down step by step.
How the Internet Works?
- You type a website’s address into your browser (e.g., www.example.com).
- Your computer sends a request to your Internet Service Provider (ISP).
- The ISP forwards the request to various servers across the internet, ultimately reaching the website’s server.
- The website’s server processes your request, sends back a response, and your browser displays the webpage.
Here’s how the process looks visually:
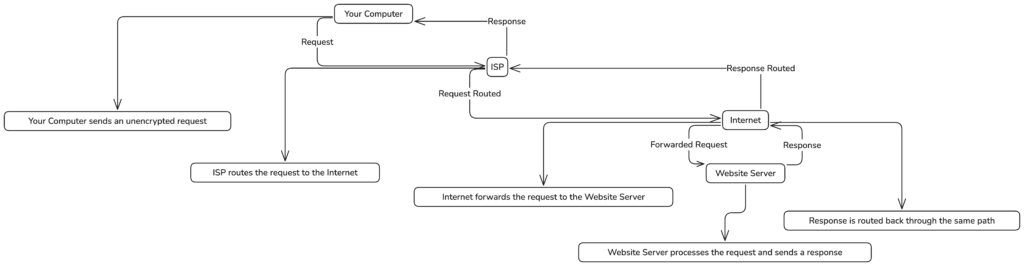
In this process, your data often travels without encryption. Anyone snooping along the path can intercept it. For instance, hackers can access sensitive information, like login credentials or private messages, especially when you’re on unsecured networks like public Wi-Fi.
Without a VPN:
Imagine you’re at a coffee shop connected to public Wi-Fi. You decide to log in to your email or access your bank account. Here’s how the data flow works in this scenario:
- Your device sends an unencrypted request through the public Wi-Fi network.
- The request passes through the coffee shop’s router and then through your ISP to the website’s server.
- The response follows the same path back to your device.
Without a VPN, the data you send and receive is vulnerable. Anyone on the same public Wi-Fi network, such as a hacker using packet-sniffing tools, can intercept this traffic. For example:
- Passwords: Hackers can capture your login credentials as plain text.
- Personal Data: Sensitive details like credit card numbers or personal messages can be stolen.
- Browsing Activity: ISPs and network administrators can monitor which websites you visit and for how long.
This lack of protection exposes you to data theft, identity fraud, and other malicious activities.
With a VPN:
When you activate a VPN, the data flow changes significantly. Here’s how it works:
- Your device connects to a secure VPN server through an encrypted tunnel.
- Any request you send (e.g., visiting a website) is encrypted before it leaves your device.
- The VPN server decrypts your request, forwards it to the website’s server, and encrypts the response before sending it back to your device.
- Only your device and the VPN server can decrypt the data, ensuring it remains secure during transmission.
The new data flow looks like this:
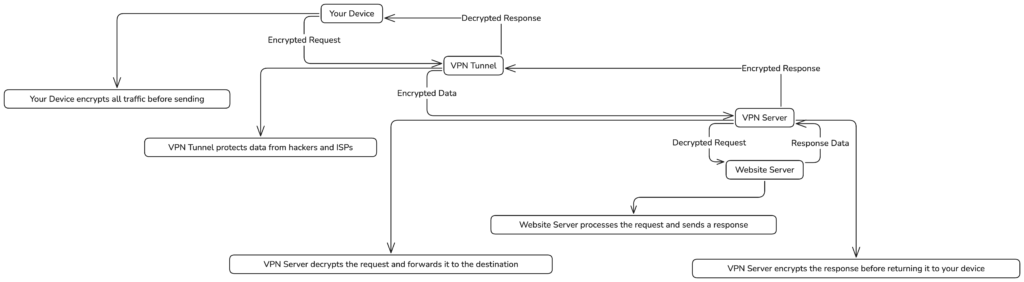
This encrypted tunnel prevents hackers, ISPs, or anyone on the same network from seeing your data or identifying your browsing activity.
Example: Public Wi-Fi Without and With VPN
Let’s revisit the coffee shop example. Without a VPN:
- You connect to the public Wi-Fi.
- A hacker on the same network uses a packet-sniffing tool to monitor the traffic.
- They intercept your login credentials while you access your email or bank account.
Now, with a VPN:
- Before connecting to the public Wi-Fi, you activate the VPN.
- Your data is encrypted and routed through the VPN server. Even if a hacker intercepts the traffic, they see only scrambled, unreadable data.
- Your IP address is replaced with the VPN server’s IP, hiding your actual location and identity.
In this way, a VPN protects your sensitive information, ensures privacy, and makes it nearly impossible for attackers or third parties to monitor your activity.
By encrypting your data and masking your IP address, a VPN creates a secure environment for online activity, even on insecure networks. This additional layer of security is invaluable for protecting your privacy and avoiding common risks like data theft or surveillance.
With this foundation in place, we can move on to why I chose OpenVPN for building my personal VPN.
Why did I choose OpenVPN?
After understanding how a VPN protects your data, the next logical question is: why choose OpenVPN for building your personal VPN? There are several VPN protocols available, such as PPTP, L2TP/IPSec, WireGuard, and OpenVPN, each with its own strengths and weaknesses. OpenVPN stands out as a versatile, secure, and open-source protocol that balances performance, customizability, and reliability.
When I decided to build my personal VPN, I chose OpenVPN because it offers the flexibility to control every aspect of the setup. Its open-source nature ensures transparency, while its robust encryption methods and support for various platforms make it a strong choice for both beginners and advanced users. Let me explain why OpenVPN is worth considering by comparing it with other popular VPN protocols.
Comparison of Popular VPN Protocols
| Feature | OpenVPN | PPTP | L2TP/IPSec | WireGuard |
|---|---|---|---|---|
| Security | Military-grade encryption (AES-256), customizable security features. Fully secure when configured properly. | Weak encryption, vulnerable to modern attacks. | Stronger encryption but slower due to double encapsulation. | Strong encryption but relatively new, less proven for long-term security. |
| Performance | Moderate speed but highly reliable. Performance depends on encryption settings. | Fast but compromises security. | Moderate speed, often slower due to extra overhead. | Extremely fast due to lean codebase. |
| Cross-Platform Support | Works on almost all platforms (Windows, macOS, Linux, Android, iOS). Highly customizable. | Supported on most platforms but with limited flexibility. | Works on most platforms but may require additional setup. | Supported on major platforms but requires kernel support. |
| Customizability | Highly customizable (port selection, protocols, and authentication methods). | Minimal options for customization. | Limited customization but supports IPSec standards. | Low customization; simplicity is prioritized. |
| Open Source | Yes, audited and trusted by the community. | No, proprietary. | Partially open (IPSec), but often relies on closed systems. | Yes, open-source but comparatively newer. |
| Ease of Setup | Moderate; requires configuration but offers great flexibility. | Simple setup, beginner-friendly. | Moderate; can be complex for beginners. | Easy to set up but lacks extensive documentation. |
| Transparency | Fully open-source with community reviews. | Proprietary, limited transparency. | Limited transparency for IPSec implementations. | Open-source but newer, requiring further scrutiny. |
| Use Cases | Best for privacy-focused users and advanced setups requiring control and flexibility. | Suitable for basic, low-security tasks (e.g., streaming). | Good for secure connections but slower performance. | Ideal for high-speed, low-latency tasks like gaming. |
Why OpenVPN Was My Choice
When I was building my VPN, I prioritized security, flexibility, and long-term reliability over raw speed. OpenVPN emerged as the best fit for the following reasons:
Security: OpenVPN provides industry-leading encryption (AES-256) and supports multiple authentication methods. Unlike PPTP, which is outdated and vulnerable to attacks, OpenVPN’s encryption ensures that data remains private and secure.
Customizability: With OpenVPN, I had complete control over how my VPN was configured. I could choose the ports to use, fine-tune encryption settings, and even integrate it with other tools like Nginx for advanced routing.
Cross-Platform Compatibility: OpenVPN works seamlessly across different operating systems, including Windows, macOS, Linux, and mobile platforms. This was crucial for me since I needed the VPN to work consistently on all my devices.
Transparency: Being open-source, OpenVPN has been reviewed and trusted by the global security community for years. This gave me confidence that there were no hidden backdoors or vulnerabilities.
Community Support: OpenVPN has a large community and detailed documentation. Whenever I encountered an issue during setup, I found abundant resources and forums that helped resolve my problems quickly.
Initially, I considered WireGuard due to its speed and simplicity. However, its relative newness made me hesitant. While WireGuard is promising, its long-term security isn’t as proven as OpenVPN. On the other hand, PPTP was ruled out immediately because of its outdated encryption and known vulnerabilities. L2TP/IPSec, while more secure than PPTP, lacked the customizability I needed for a personal VPN.
OpenVPN struck the perfect balance for my use case: a secure, flexible, and well-documented protocol with a proven track record. Its ability to adapt to complex setups while maintaining robust encryption made it the clear choice.
By using OpenVPN for your personal VPN, you can ensure your online privacy and security without compromising on flexibility or reliability. In the next section, I’ll guide you through the exact steps I took to set up my personal VPN using AWS EC2 and OpenVPN. Let’s get started!
Why AWS?
You might be wondering: “Why use AWS for my VPN when other hosting providers exist?” Indeed, services like Linode, DigitalOcean, and Vultr also offer virtual private servers at competitive prices. Each option has its strengths. Here’s why I chose AWS, along with a quick comparison table to help you make the best choice for your needs:
- Familiarity: If you already work with AWS or are learning DevOps and cloud management, staying in one ecosystem can simplify your workflow.
- Free Tier for New Accounts: For up to 12 months, AWS offers a Free Tier (e.g., t2.micro or t3.micro instances). This can be enough to experiment with a VPN without incurring large costs—so long as you monitor usage (particularly data transfer).
- Global Reach & Advanced Services: AWS has a vast global infrastructure with many regions and availability zones. It also offers robust tooling (e.g., CloudWatch for monitoring, IAM for fine-grained access control, etc.). If you plan on integrating your VPN with other AWS services down the line, it can be convenient to stay on the same platform.
That said, AWS is not always the cheapest or simplest option—especially after the Free Tier expires. Egress (outbound) data can become expensive, and AWS’s billing model is more complex than many flat-rate VPS providers. So below is a quick side-by-side comparison to help you decide which provider fits your budget and requirements:
| Provider | AWS (Amazon Web Services) | Linode | DigitalOcean | Vultr |
|---|---|---|---|---|
| Cheapest Plan | Free Tier for 12 months (t2.micro/t3.micro). Once expired, pay-as-you-go. Rates vary by instance + data egress fees. | Starting at $5/month with predictable pricing. | Starting at $5/month “Basic Droplet.” Data transfer limits are higher than AWS but still watch usage. | Starting at $5/month. Similar to Linode and DigitalOcean for pricing. |
| Cost Complexity | Medium/High. Pricing structure can be confusing. Egress data can add up quickly. | Low. Straightforward monthly or hourly billing. | Low. Straightforward monthly or hourly billing. | Low. Straightforward monthly or hourly billing. |
| Ease of Setup | More advanced. AWS Console and services can feel overwhelming for newcomers. Excellent documentation but steep learning curve. | Very user-friendly. Plenty of one-click apps and guides. | Also user-friendly. One-click app marketplace, large community tutorials. | Similar to Linode/DO with a user-friendly control panel and one-click setups. |
| Scalability | Extremely high. You can easily scale up (or horizontally) to enterprise levels. | Good. Linode supports easy resizing and has multiple data center locations. | Good. DigitalOcean also supports vertical/horizontal scaling with Droplets. | Good. Vultr offers quick server resizing and many data center locations. |
| Data Center Locations | Numerous global regions (North America, South America, Europe, Asia-Pacific, etc.). | 11 data centers worldwide. | 13 data centers worldwide. | 17 data centers worldwide. |
| Ecosystem & Integrations | Vast. Integrate with services like S3, RDS, IAM, CloudWatch, etc. | Primarily focused on cloud servers and related add-ons (load balancers, etc.). | Primarily focused on cloud servers and related add-ons (managed DB, etc.). | Primarily focused on VPS hosting and related services. |
So,
- If you’re new to AWS, you can leverage the 12-month Free Tier to experiment with OpenVPN. Just keep an eye on usage and remember that heavy data transfers or upgrades to larger instances will incur charges.
- If you prefer predictable billing or want a simpler dashboard, Linode, DigitalOcean, or Vultr might be more cost-effective. They have straightforward monthly rates and decent bandwidth packages included.
- If you need advanced cloud services or plan to scale significantly (e.g., integrate with a large web app, run complex workloads), AWS is arguably more powerful and feature-rich. But that power comes with a steeper learning curve and potentially higher costs once you go beyond the Free Tier limits.
Overall, it’s important to pick the provider that meets your specific needs—whether that’s budget, simplicity, or future-proofing for growth and advanced cloud functionality.
Prerequisites
Before setting up your personal VPN, there are a few essential preparations to ensure a smooth process. This section outlines everything you need to have in place, strictly based on the provided instructions and videos.
1. AWS Account
You’ll need an active AWS account to access the AWS Management Console. If you don’t already have one:
- Sign up at AWS Free Tier. AWS provides 12 months of free usage for certain services, including 750 hours/month of usage for t2.micro EC2 instances.
- Ensure you have a valid payment method added to your account. While this setup qualifies under the Free Tier, exceeding the limits may result in charges.
2. AWS Marketplace: OpenVPN AMI
AWS provides pre-configured virtual machine images (Amazon Machine Images or AMIs) for deploying OpenVPN. During the setup process, you’ll search for OpenVPN in the AWS Marketplace and select the first result. This pre-built AMI simplifies the installation process and eliminates the need to manually download or configure OpenVPN.
Key Details to Know:
- The OpenVPN Access Server AMI handles both VPN configuration and administration tasks.
- This AMI includes a web-based admin panel for managing VPN users, configurations, and monitoring.
3. Key Pair for EC2 Access
When launching an EC2 instance, AWS requires a key pair for secure access via SSH. If you don’t already have one:
- Create a new key pair during the instance setup process.
- Save the
.pemfile securely, as you’ll need it to connect to your instance later.
4. Internet Connection
A stable and reliable internet connection is essential for:
- Accessing the AWS Management Console.
- Connecting to your EC2 instance via SSH for configuration.
- Testing the VPN once it’s set up.
5. Networking Knowledge (Optional)
Although this guide provides step-by-step instructions, having a basic understanding of:
- IP addresses: Knowing how public IPs work will help you connect to your VPN server.
- Ports: Port 22 (for SSH) and port 1194 (for VPN traffic) will be used in the setup.
6. AWS Region Selection
Choose an AWS region close to your physical location. A nearby region reduces latency, ensuring faster and more reliable VPN performance.
With these prerequisites in place, you’re ready to begin setting up your EC2 instance and configuring OpenVPN. In the next section, we’ll walk through the detailed step-by-step process. Let’s move forward!
Installing and Configuring OpenVPN on AWS EC2
Setting up your personal VPN involves launching an EC2 instance, installing the OpenVPN Access Server from the AWS Marketplace, configuring the server, and securely connecting devices. This step-by-step guide ensures no detail is overlooked, following the resources provided.
Step 1: Launching an EC2 Instance with OpenVPN
The first step in building your personal VPN is creating an EC2 instance on AWS and installing OpenVPN. This section explains the process meticulously, ensuring that every choice you make is well-informed.
1. Log In to the AWS Management Console
- Go to the AWS website (aws.amazon.com) and log in with your credentials.
- Navigate to the EC2 Dashboard by selecting EC2 under the “Compute” section in the AWS Management Console.

2. Launch a New EC2 Instance
- In the EC2 Dashboard, click Launch Instance. This opens the instance creation wizard.
- In the “Name and tags” section, assign a descriptive name to your instance (e.g.,
MyVPNServer). This helps identify the instance among others you may create in the future.
3. Select an Amazon Machine Image (AMI)

Search for OpenVPN in AWS Marketplace:
- In the Application and OS Images (Amazon Machine Image) section, select AWS Marketplace AMIs.
- In the search bar, type
OpenVPN Access Serverand press Enter.
Choose the First Option:

- From the results, choose the OpenVPN Access Server / Self-Hosted VPN (first option). Here’s why:
- Free Tier Eligibility: The first option is included in AWS Free Tier, which makes it cost-effective for personal use.
- Designed for Individual Devices: This option supports secure VPN connections for individual users and small-scale deployments. Larger options (e.g., “10 Connected Devices”) are designed for team or enterprise use, which isn’t necessary here.
- Pre-Configured: It comes with all essential configurations for quickly deploying a personal VPN.
- From the results, choose the OpenVPN Access Server / Self-Hosted VPN (first option). Here’s why:
Understand What This AMI Offers:
- Pre-installed OpenVPN Access Server: Includes the OpenVPN server software and a web-based admin panel for managing users and settings.
- Supports Self-Hosted VPN: Enables secure site-to-site or remote access connections without relying on third-party providers.
- System: Built on Ubuntu 22.04 LTS for long-term stability and security.
- Cost: Listed as $0.023 per hour on a t2.micro instance. However, under the Free Tier, there’s no charge for eligible users.
Subscribe to the AMI:
- After selecting the AMI, you’ll see two subscription options:
- Subscribe Now: Immediately subscribes to the AMI, allowing you to review and configure it later.
- Subscribe on Instance Launch: Subscribes to the AMI automatically when the instance is launched.
- Click Subscribe Now to avoid delays during the launch process. Confirm the subscription terms and proceed.
- After selecting the AMI, you’ll see two subscription options:
4. Choose the Instance Type
- Select t2.micro:
- In the Instance Type section, choose t2.micro. It is eligible for the AWS Free Tier, which provides 750 hours of usage per month for 12 months.
- Why t2.micro?
- It offers sufficient resources (1 vCPU and 1 GB RAM) for personal VPN setups.
- Free Tier eligibility makes it cost-efficient for individual users.
5. Configure Instance Details
- Enable Auto-Assign Public IP:
- Ensure that Auto-Assign Public IP is enabled. This assigns a public IP address to your instance, making it accessible for VPN configuration and client connections.
- Public IPs are essential for connecting to the VPN server from external devices.
6. Review and Launch
Key Pair:
- Select an existing key pair or create a new one. This key pair is critical for SSH access to the instance.
- Save the
.pemfile securely, as losing it will lock you out of the instance.
Network Settings:
- Configure the security group to include:
- Port 22 (SSH): Allows secure access to the instance for configuration.
- Port 1194 (UDP): The default port for OpenVPN traffic.
- Port 443 (HTTPS): Provides access to the web-based admin panel.
- Configure the security group to include:
Launch Instance:
- Review all configurations carefully.
- Click Launch Instance to deploy the server. AWS will initialize the instance, which may take a few minutes.
Once your instance is running, you’ll connect to it via SSH to complete the OpenVPN setup and configuration. The next section will guide you through these steps in detail, ensuring your VPN server is ready for use.
Step 2: Accessing and Configuring OpenVPN
After successfully launching the EC2 instance with the OpenVPN Access Server, the next step is to connect to the instance via SSH, configure the server, and prepare it for use. This section walks you through the entire process with detailed instructions and terminal commands.
1. Connect to the Instance via SSH
To start configuring OpenVPN, you must connect to the EC2 instance using SSH. Follow these steps:
Open a Terminal or PowerShell:
- For macOS or Linux users, use the built-in Terminal.
- For Windows users, use PowerShell or an SSH client like PuTTY.
Locate Your Key Pair File:
- Ensure the
.pemfile (your private key) is saved in a secure and accessible location. You’ll need this file to establish the SSH connection.
- Ensure the
Get the Public IP of the Instance:
- In the AWS Management Console, go to the EC2 Dashboard.
- Select the instance you launched and copy its Public IPv4 Address.
Run the SSH Command:
Use the following command to connect as the root user:
ssh -i /path/to/your-key.pem root@<Public_IP>Replace
/path/to/your-key.pemwith the location of your key file and<Public_IP>with the instance’s public IP address.
Accept the Connection:
On your first connection, you may see a warning like this:
The authenticity of host 'ec2-54-158-246-62.compute-1.amazonaws.com' can't be established.Type yes to accept the connection and proceed.
2. Switch to the OpenVPN Admin User
After connecting as the root user, you need to switch to the openvpnas user account to configure the OpenVPN server:
Switch to the Admin User:
Use the following command:
ssh -i /path/to/your-key.pem openvpnas@<Public_IP>
Configure OpenVPN:
- Once connected, OpenVPN Access Server will prompt you to complete the initial configuration. Follow the on-screen instructions:
- Accept the licensing agreement by typing yes.
- Set an admin password for the OpenVPN server.
- Once connected, OpenVPN Access Server will prompt you to complete the initial configuration. Follow the on-screen instructions:
3. Access the OpenVPN Admin Panel
Locate the Admin Panel URL:
After the initial configuration, the terminal will display the URL for the admin panel. It typically follows this format:
https://<Public_IP>:943/admin
Log in to the Admin Panel:
- Open a web browser and navigate to the provided URL.
- If you encounter an SSL warning, bypass it (the connection is secure but uses a self-signed certificate).
- Use the default credentials:
- Username:
openvpn - Password: The one you just set during the configuration.
- Username:
4. Final Configuration in the Admin Panel
Once logged in to the admin panel, complete the setup by adjusting the following settings:
Change the Default Admin Password:
- Navigate to the “User Management” section.
- Update the password for the
openvpnadmin account to ensure security.
Set Up VPN Users:
- Add new users by creating accounts in the admin panel. Assign passwords and download their respective
.ovpnconfiguration files.
- Add new users by creating accounts in the admin panel. Assign passwords and download their respective
Network Configuration:
- Configure routing and subnet settings to define how connected devices will access the internet and other network resources.
Ports and Protocols:
- Verify that port 1194 (UDP) is open for VPN traffic and adjust other settings as needed.
5. Downloading the VPN Client
After completing the configuration in the admin panel, you need to download the VPN client application for your device. This step ensures that you can establish a secure connection to your VPN server.

Access the Client Web Interface:
Open a browser and navigate to the OpenVPN client portal using the following URL:
https://<Public_IP>:943Replace
<Public_IP>with the public IPv4 address of your EC2 instance.
Log In to the Portal:
- Use the user credentials you created earlier or the default user credentials (
openvpnusername and the password you set during the configuration). - You’ll be directed to the OpenVPN Access Server User Interface, which provides options for downloading the VPN client.
- Use the user credentials you created earlier or the default user credentials (
Download the OpenVPN Client:
- The portal will display client options based on your device. For example:
- macOS: If you’re on a Mac, the portal will suggest downloading the OpenVPN Connect app for macOS.
- Windows, Linux, Android, and iOS: Icons for these platforms are also available for downloading the appropriate client.
- Click on the icon matching your operating system to download the OpenVPN Connect app.
- The portal will display client options based on your device. For example:
Download Your Connection Profile:
Below the client icons, you’ll see Available Connection Profiles. Click the link that says:
Yourself (user-locked profile)This downloads a
.ovpnfile, which contains the connection settings specific to your VPN server and user account.
Save the Files:
- Save the downloaded client application and the
.ovpnconfiguration file in a secure and easily accessible location on your device.
- Save the downloaded client application and the
6. Install and Configure the VPN Client
Install the Client:
- Open the downloaded OpenVPN Connect installer and follow the on-screen instructions to install the client on your device.
Import the Configuration File:
- Launch the OpenVPN Connect application.
- Import the
.ovpnfile by either dragging it into the app or selecting it manually through the interface.
Connect to the VPN:
- After importing the profile, click Connect.
- Enter your VPN user credentials (username and password) when prompted.
Verify the Connection:
- Once connected, the app will display your VPN connection status.
- To ensure the VPN is working, visit WhatIsMyIP and confirm that your public IP matches your VPN server’s IP.
7. Test the OpenVPN Server
Verify Server Status:
Run the following command in the terminal to check if OpenVPN is running:
sudo service openvpnas status
Test Connectivity:
- Connect a device to the VPN using the configuration file downloaded from the admin panel.
- Verify that your public IP changes to the server’s IP and that the connection is encrypted.
By following these steps, you’ll successfully access and configure your OpenVPN server, making it ready for secure connections. In the next section, we’ll cover how to connect devices and test the VPN functionality.
Step 3: Testing and Verifying the VPN
Check Your IP Address
- Visit WhatIsMyIP to confirm that your public IP matches the VPN server’s IP.
Verify DNS Leak Protection
- Use a DNS leak testing tool like DNSLeakTest to ensure that all DNS queries are routed through the VPN.
Test the Connection
- Try accessing region-locked content or private resources to confirm the VPN is working as intended.
By following these steps, you’ll successfully launch and configure OpenVPN on AWS EC2, connect your devices, and ensure your VPN is secure and fully operational. With the VPN in place, you now have a powerful tool to protect your online privacy and secure sensitive data.
Best Practices for Using Your VPN
Once your personal VPN is set up and running, it’s essential to follow best practices to ensure its security, performance, and usability. By implementing these practices, you can maintain a safe and efficient VPN environment while minimizing risks.
1. Regularly Update OpenVPN and Server Software
- Why It’s Important: Keeping your OpenVPN server and client software up-to-date ensures you’re protected against the latest security vulnerabilities.
- How to Update:
On the EC2 instance, check for updates using:
sudo apt update && sudo apt upgrade -yRegularly visit the OpenVPN website to download the latest client versions for your devices.
2. Use Strong and Unique Passwords
- Why It’s Important: Weak passwords are an easy target for attackers. Using strong, unique passwords for both the admin panel and VPN users adds an extra layer of security.
- How to Set a Strong Password:
- Include at least 12 characters with a mix of uppercase, lowercase, numbers, and special characters.
- Avoid using easily guessable passwords (e.g., “password123”).
- Periodically change passwords for all VPN users.
3. Restrict Access to Your VPN Server
- Why It’s Important: Limiting access reduces the attack surface of your VPN server.
- How to Restrict Access:
Configure your AWS security group to allow access only from specific IP addresses for SSH (port 22) and VPN traffic (port 1194).
For example, update your security group rules to include only your home or office IP address.
Use this command to confirm security group updates:
aws ec2 describe-security-groups
4. Monitor VPN Activity
- Why It’s Important: Regular monitoring helps detect unusual or unauthorized activity.
- How to Monitor:
- Use the OpenVPN admin panel to review connection logs and user activity.
- Set up alerts for suspicious activities, such as repeated failed login attempts.
5. Enable Multi-Factor Authentication (MFA)
- Why It’s Important: MFA adds an additional layer of security to your admin panel by requiring a second factor (e.g., a one-time code) for login.
- How to Enable MFA:
- Use an authenticator app (e.g., Google Authenticator) and configure it in the OpenVPN admin panel.
- Follow OpenVPN’s MFA setup guide for step-by-step instructions.
6. Rotate Encryption Keys
- Why It’s Important: Regularly rotating encryption keys ensures that even if a key is compromised, the exposure is limited.
- How to Rotate Keys:
Generate new client configuration files (
.ovpn) periodically for all users.Revoke old keys using:
sudo ./revoke-client.sh <client-name>Update users with new
.ovpnfiles.
By following these best practices, you can maintain a secure, reliable, and high-performing VPN that protects your online activities while ensuring peace of mind.
Here is the detailed video which you can follow:
Conclusion
Building your personal VPN using AWS EC2 and OpenVPN is not just a practical solution for enhancing online security but also an empowering way to take control of your privacy. Unlike commercial VPNs, a personal VPN gives you complete authority over configurations, user access, and data handling. Through this guide, you’ve learned how to set up an EC2 instance, configure OpenVPN, and establish secure connections across devices.
This setup provides a cost-effective, scalable, and reliable way to safeguard sensitive data and maintain anonymity online. Whether you’re a developer, a privacy enthusiast, or someone who frequently works on public Wi-Fi, this DIY approach is a step toward a more secure digital presence.
As you move forward, remember to follow the best practices outlined in this guide to ensure your VPN remains secure and efficient. With the power of OpenVPN and AWS at your fingertips, you now have the tools to protect your online activity, anywhere, anytime.
FAQs
What are the costs of running a personal VPN on AWS?
If you use a t2.micro instance, the AWS Free Tier provides 750 hours of free usage per month for the first 12 months. Beyond that:
t2.micro instance: ~$0.0116 per hour.
Additional costs: Data transfer outside AWS (first 1 GB per month is free; beyond that, charges apply based on the region).
Can I add multiple users to my VPN?
Yes, OpenVPN Access Server allows you to create multiple user accounts. You can add users through the admin panel by assigning individual credentials and generating unique .ovpn configuration files for each user.
How secure is OpenVPN compared to other VPN protocols?
OpenVPN is one of the most secure VPN protocols available. It uses AES-256 encryption, offers robust authentication methods, and supports both UDP and TCP for flexible configurations. When configured properly, it is more secure than older protocols like PPTP or L2TP/IPSec.
Can I use this VPN on mobile devices?
Absolutely! OpenVPN supports iOS and Android. You can download the OpenVPN Connect app from the App Store or Google Play, import your .ovpn file, and connect seamlessly.
How do I troubleshoot connectivity issues?
If you encounter issues:
1. Ensure the EC2 instance is running.
2. Verify that the correct ports (1194 for VPN and 443 for HTTPS) are open in your AWS security group.
3. Check your VPN client logs for error messages.
4. Restart the OpenVPN server using: sudo service openvpnas restart
What happens if I lose my SSH key?
If you lose your .pem file, you will not be able to SSH into your EC2 instance. To regain access:
1. Use the AWS Systems Manager Session Manager if enabled.
2. Otherwise, you’ll need to create a new key pair and associate it with your instance using AWS instance recovery steps.
Can I switch to a different AWS region after setup?
Switching regions requires you to stop the instance, create an AMI, and launch a new instance in the desired region. You’ll also need to update your .ovpn files with the new server’s IP address.
How do I test if my VPN is working?
Check your IP address at WhatIsMyIP. If the displayed IP matches your VPN server’s IP, your connection is secure.
Use DNSLeakTest to ensure no DNS leaks are occurring.
Is it possible to scale this VPN setup for a small team?
Yes, OpenVPN Access Server supports scaling for small teams or organizations. For larger teams, consider upgrading your EC2 instance to a higher tier (e.g., t3.medium) to accommodate increased traffic and user load.